Mastering Encryption: Step-by-Step Guide for Creating Your Own Encryption Algorithm
-
Quick Links:
- Introduction to Encryption Algorithms
- Understanding Encryption
- Different Types of Encryption Algorithms
- Designing Your Own Encryption Algorithm
- Implementing the Algorithm in Code
- Testing Your Encryption Algorithm
- Real-World Case Studies
- Best Practices for Encryption
- Conclusion
- FAQs
Introduction to Encryption Algorithms
In today’s digital world, data security is paramount. With the rise of cyber-attacks and data breaches, understanding how to create encryption algorithms is essential for protecting sensitive information. This guide will take you through the process of creating your own encryption algorithm, covering everything from the basics to advanced techniques.
Understanding Encryption
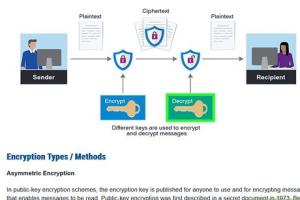
Encryption is the process of converting data into a code to prevent unauthorized access. It uses algorithms to transform plaintext into ciphertext, making it unreadable without a decryption key. This section will delve deeper into the principles of encryption, including symmetric and asymmetric encryption.
What is Symmetric Encryption?
Symmetric encryption uses the same key for both encryption and decryption. It is faster and is suitable for encrypting large amounts of data. Common symmetric algorithms include AES (Advanced Encryption Standard) and DES (Data Encryption Standard).
What is Asymmetric Encryption?
Asymmetric encryption utilizes a pair of keys: a public key for encryption and a private key for decryption. This method is more secure but slower than symmetric encryption. RSA (Rivest-Shamir-Adleman) is a well-known asymmetric algorithm.
Different Types of Encryption Algorithms
Before you create your own encryption algorithm, it's crucial to understand the various types available. This section will explore popular encryption algorithms and their characteristics.
- Data Encryption Standard (DES) - An older standard that is now considered less secure.
- AES (Advanced Encryption Standard) - A widely used symmetric algorithm that offers strong security.
- RSA (Rivest-Shamir-Adleman) - A widely used asymmetric algorithm that provides secure data transmission.
- Blowfish - A fast block cipher that is a good alternative to AES.
Designing Your Own Encryption Algorithm
Designing an encryption algorithm requires careful consideration of various factors, including security, efficiency, and ease of implementation. Here’s a step-by-step approach to designing your own encryption algorithm:
Step 1: Define Your Objectives
Start by defining what you want to achieve with your encryption algorithm. Consider factors like:
- Speed of encryption and decryption
- Level of security required
- Types of data you will be encrypting
Step 2: Choose Your Method
Select whether you want to use symmetric or asymmetric encryption based on your objectives. For example, if you need to encrypt large files quickly, symmetric encryption may be preferable.
Step 3: Develop the Algorithm
Now, you can start developing the algorithm. Below is a simplified example of how to create a basic symmetric encryption algorithm:
function simpleEncrypt(plaintext, key) {
let encrypted = "";
for (let i = 0; i < plaintext.length; i++) {
// Simple XOR encryption
encrypted += String.fromCharCode(plaintext.charCodeAt(i) ^ key.charCodeAt(i % key.length));
}
return encrypted;
}
Step 4: Analyze Security
Once your algorithm is developed, analyze its security. Consider potential attack vectors, such as:
- Brute force attacks
- Cryptanalysis
- Side-channel attacks
Implementing the Algorithm in Code
After designing your encryption algorithm, the next step is to implement it in code. Depending on your programming language of choice, the implementation can vary. Here’s an example using Python:
def simple_encrypt(plaintext, key):
encrypted = ""
for i in range(len(plaintext)):
encrypted += chr(ord(plaintext[i]) ^ ord(key[i % len(key)]))
return encrypted
Testing Your Encryption Algorithm
Testing is crucial to ensure your encryption algorithm works as intended. Perform unit tests, integration tests, and security testing to validate its efficacy. Consider the following:
- Test with different types of data
- Check for performance under load
- Assess resilience against attacks
Real-World Case Studies
Understanding how encryption algorithms have been used in real-world applications can provide valuable insights. Here are a few notable case studies:
Case Study 1: AES in Wi-Fi Security
The Advanced Encryption Standard (AES) is pivotal in securing Wi-Fi networks. It protects data transmission between devices, ensuring confidentiality and integrity.
Case Study 2: RSA in Secure Online Transactions
RSA encryption is widely used in online banking and e-commerce. It secures transactions by encrypting sensitive information, making it unreadable to unauthorized parties.
Best Practices for Encryption
Implementing best practices in your encryption strategy can enhance security. Consider the following:
- Regularly update encryption algorithms to counteract advancements in cryptanalysis.
- Use strong, complex keys and manage them securely.
- Educate users about the importance of encryption and secure practices.
Conclusion
Creating your own encryption algorithm can be a rewarding challenge. By understanding the principles of encryption, designing a robust algorithm, and implementing it correctly, you can significantly enhance data security. Remember to stay informed about best practices and continuously test and update your algorithms to protect against evolving threats.
FAQs
1. What is an encryption algorithm?
An encryption algorithm is a method of transforming data into a secure format to prevent unauthorized access.
2. What are the types of encryption algorithms?
There are two main types: symmetric and asymmetric encryption algorithms.
3. How do I choose the right encryption algorithm?
Consider the type of data, the required speed, and the level of security needed.
4. Is symmetric encryption faster than asymmetric encryption?
Yes, symmetric encryption is generally faster and suitable for large data sets.
5. Can I use my own encryption algorithm for production?
It's recommended to use established algorithms unless your custom implementation is thoroughly tested and vetted.
6. How can I test my encryption algorithm?
Conduct unit tests, performance tests, and security assessments to ensure its reliability.
7. What is key management?
Key management involves generating, storing, and protecting cryptographic keys used in encryption algorithms.
8. What are common encryption algorithms?
Common algorithms include AES, RSA, DES, and Blowfish.
9. Is encryption foolproof?
No encryption is entirely foolproof, but strong encryption significantly reduces risks.
10. How often should I update my encryption methods?
Regular updates are essential, especially as new vulnerabilities are discovered.
Random Reads
- How to set up external hard drive wii u
- How to set up ftp between two computers
- Where to find clipboard iphone
- Why did your discord server disappear
- The ultimate guide to deleting devices from your spotify account
- Remove fingerprints tv screen
- Remove furniture dents from carpet
- How to make godzilla in little alchemy
- Ultimate guide to download youtube videos macos
- Mastering numeric keypad best practices