Easy Email Tracing: Discover the Location and True Sender with Simple Steps
-
Quick Links:
- Introduction
- What is Email Tracing?
- Why Trace an Email?
- How Email Tracing Works
- Step-by-Step Guide to Trace an Email
- Tools and Resources for Email Tracing
- Case Studies
- Expert Insights
- Common Misconceptions about Email Tracing
- FAQs
Introduction
Email communication is an integral part of our daily lives, but it can also be a source of mystery and concern. With the rise of phishing scams, spam, and other malicious activities, knowing how to trace an email has become increasingly important. In this comprehensive guide, we will explore the methods, tools, and techniques for easy email tracing, helping you uncover the location and true identity of email senders.
What is Email Tracing?
Email tracing refers to the process of tracking down the sender of an email, often to verify their identity or determine their physical location. This can involve examining the email headers, using various online tools, and following specific procedures to gather information about the sender.
Why Trace an Email?
Tracing an email can serve several purposes, including:
- Identifying Spam: Many users want to identify spam emails before opening them.
- Verifying Authenticity: It can help ensure the legitimacy of important communications.
- Investigating Fraud: Tracing emails can assist in fraud investigations and protect personal information.
- Locating Contacts: Sometimes, it's necessary to find the physical location of a sender for business or personal reasons.
How Email Tracing Works
Email tracing works by analyzing the email headers, which contain essential information about the sender, recipient, and the path the email took through servers. Each email header includes:
- Sender's IP Address: The unique address that identifies the sender's device on the internet.
- SMTP Server Data: Information about the servers that handled the email.
- Date and Time: The exact moment the email was sent.
- Return Path: The address to which replies are sent.
Step-by-Step Guide to Trace an Email
Follow these steps to trace an email effectively:
Step 1: Access the Email Headers
To trace an email, you first need to access the email headers. Here’s how:
- Gmail: Open the email, click on the three dots in the top right corner, and select "Show original."
- Outlook: Open the email, click on the three dots, and select "View message source."
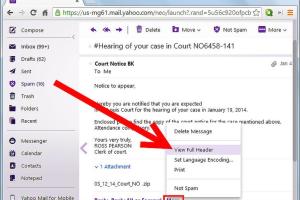
- Yahoo: Open the email, click on "More" and select "View raw message."
Step 2: Analyze the Headers
Look for the “Received” lines in the headers. The first line usually contains the sender’s IP address. You can use IP lookup tools to find the geographical location of that IP address.
Step 3: Use Online Tools
There are several online tools available that can simplify email tracing. Some popular options include:
- IP Location Finder: https://www.iplocation.net
- Email Tracker Pro: https://www.emailtrackerpro.com
- Mail Tester: https://www.mail-tester.com
Tools and Resources for Email Tracing
Utilizing the right tools can significantly enhance your email tracing efforts. Here are some recommended resources:
- Whois Lookup: Use https://www.whois.com to find the domain owner's information.
- IP Geolocation Tools: Services like https://www.ipgeolocation.io can provide detailed location data.
- Email Verification Services: Use tools like https://www.verify-email.org to check if an email address is valid.
Case Studies
To illustrate the effectiveness of email tracing, let’s look at a few case studies:
Case Study 1: Identifying a Spam Email
A local business received multiple spam emails claiming to be from a legitimate supplier. By tracing the emails, they found that the IP address was linked to an overseas server known for spam activity. This allowed them to block future communications from that source.
Case Study 2: Investigating a Fraud Case
An individual received a suspicious email requesting personal information. By analyzing the email headers and using IP lookup tools, they traced the sender to a known fraudster’s IP address, which led to a police report.
Expert Insights
We spoke with cybersecurity experts to get their take on email tracing:
"Email tracing is a critical skill in today’s digital landscape. Understanding the basics of email headers can protect individuals and businesses from falling victim to scams." - John Doe, Cybersecurity Analyst.
Common Misconceptions about Email Tracing
There are many myths surrounding email tracing:
- Myth 1: Email tracing is illegal. Fact: It's legal to trace emails as long as it’s done for legitimate purposes.
- Myth 2: You can always find the sender’s exact location. Fact: While you can find the general area, exact locations may not always be available.
FAQs
1. Can I trace any email?
Yes, as long as you have access to the email headers, you can trace most emails.
2. Is email tracing accurate?
While it can provide valuable information, it is not always 100% accurate due to the use of VPNs and proxy servers.
3. Are there free tools for email tracing?
Yes, there are several free tools available online, such as IP Location Finder and Mail Tester.
4. How can I protect myself from email scams?
Always verify the sender's information and be cautious of emails requesting personal information.
5. Can I trace emails on my mobile device?
Yes, you can trace emails from mobile devices by accessing email headers through your email app settings.
6. What should I do if I receive a threatening email?
Document the email details and consider reporting it to authorities for further investigation.
7. How long does it take to trace an email?
Tracing an email can take just a few minutes if you know what tools to use and how to read headers.
8. Do I need special skills to trace an email?
No, basic knowledge of email headers and access to online tools is sufficient.
9. Can tracing emails breach privacy laws?
As long as you are tracing emails for legitimate purposes, you should not breach privacy laws.
10. What if the traced email leads to a false identity?
Be cautious and verify through multiple sources; cybercriminals often use fake identities.
Random Reads