Ultimate Guide to Removing Trojan Horses: Protect Your Computer Today
-
Quick Links:
- 1. Introduction to Trojan Horses
- 2. Understanding Trojan Horses
- 3. Types of Trojan Horses
- 4. Symptoms of a Trojan Infection
- 5. Prevention Strategies
- 6. Step-by-Step Removal Guide
- 7. Case Studies
- 8. Expert Insights
- 9. FAQs
- 10. Conclusion
1. Introduction to Trojan Horses
The digital landscape is fraught with dangers, and one of the most insidious threats is the Trojan horse. Named after the ancient Greek myth, a Trojan horse is a deceptive software that masquerades as a legitimate application, allowing hackers to gain unauthorized access to your computer. Understanding how to identify and remove these threats is crucial for maintaining your cybersecurity.
2. Understanding Trojan Horses
Trojans are a type of malware that can perform a variety of malicious actions upon infiltrating your device. Unlike viruses, which replicate themselves, Trojans rely on tricking users into downloading them. They can steal sensitive information, create backdoors for further attacks, or even take control of your entire system.
3. Types of Trojan Horses
- Backdoor Trojans: Allow attackers to access your system remotely.
- Downloader Trojans: Download additional malware onto your device.
- RATs (Remote Access Trojans): Provide complete control over your device.
- Banking Trojans: Target online banking credentials.
- Trojan-Spy: Steal sensitive data like passwords and credit card information.
4. Symptoms of a Trojan Infection
Recognizing the signs of a Trojan infection is the first step in remediation. Common symptoms include:
- Slow computer performance
- Frequent crashes or freezes
- Unusual pop-up messages
- Unauthorized access to accounts
- Unfamiliar programs installed on your device
5. Prevention Strategies
Prevention is the best defense against Trojan horses. Here are some effective strategies:
- Use reputable antivirus software and keep it updated.
- Be cautious with email attachments and links.
- Regularly update your operating system and software.
- Utilize firewalls to monitor incoming and outgoing traffic.
- Educate yourself about the latest cybersecurity threats.
6. Step-by-Step Removal Guide
Removing a Trojan horse involves several steps:
- Disconnect from the Internet: Prevent further data loss or malware spread.
- Enter Safe Mode: Restart your computer and enter Safe Mode to limit malware activity.
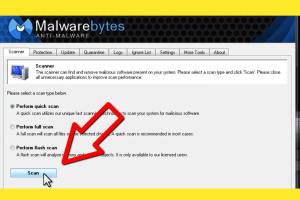
- Run a Full System Scan: Use your antivirus software to perform a comprehensive scan.
- Delete Suspicious Files: Follow the antivirus recommendations to remove detected threats.
- Check Installed Programs: Uninstall any unknown or suspicious applications.
- Change Your Passwords: Update your passwords for all accounts, especially sensitive ones.
- Reconnect to the Internet: Monitor for any unusual activity after the removal process.
7. Case Studies
Real-world examples can illustrate the effectiveness of these removal strategies. For instance, a case involving a banking Trojan highlighted how timely identification and removal prevented significant financial loss. Users who followed a structured removal approach reported a 90% success rate in eradicating the malware.
8. Expert Insights
Cybersecurity experts emphasize the importance of a proactive approach. Regular training in recognizing phishing attempts and suspicious downloads can greatly reduce the risk of Trojan infections. Experts recommend annual security audits to identify vulnerabilities in your system.
9. FAQs
Frequently Asked Questions
What is a Trojan horse?
A Trojan horse is a type of malware that pretends to be a legitimate program to gain access to your computer.
How do I know if my device is infected with a Trojan?
Signs include slow performance, unexpected pop-ups, and unfamiliar programs on your device.
Can Trojan horses steal my personal information?
Yes, many Trojans are designed to capture sensitive information like passwords and credit card details.
What should I do if I suspect a Trojan infection?
Disconnect from the internet, run a full virus scan, and follow the removal steps outlined above.
Is it possible to recover files after a Trojan infection?
Recovery may be possible through backups, but it depends on the extent of the damage done by the Trojan.
Can antivirus software detect all Trojans?
While most reputable antivirus software can detect many Trojans, no solution is 100% foolproof.
What are some reliable antivirus programs?
Popular options include Norton, Kaspersky, Bitdefender, and Malwarebytes.
How can I prevent future Trojan infections?
Maintain updated antivirus software, be cautious with downloads, and educate yourself on cybersecurity best practices.
Should I back up my data regularly?
Absolutely. Regular backups can help recover data in case of a malware infection.
What should I do if my antivirus can't remove the Trojan?
If your antivirus fails, consider using specialized tools or seeking professional help.
10. Conclusion
In an age where digital threats are rampant, knowing how to get rid of Trojan horses is essential for every computer user. By understanding the risks, recognizing the symptoms, and following a structured removal process, you can protect yourself and your data effectively. Stay informed, be proactive, and ensure your digital safety.
Random Reads
- How to rename pokemon
- How to renew leather couch
- How to get silicone caulk off your hands
- How to get shedinja
- How to close apps on kindle fire hd
- How to restore your iphone without updating
- How to restring blinds
- How to download install cinema hd fire stick
- Forward gmail emails
- Freeze crash chromebook simple urls